Learn what are the Best DDoS tool everyone should have
Many people question what DDoS is, what is a DDoS attack precisely, and what does DDoS represent? The distributed denial-of-service attack is short for DDoS. DDoS attacks take place when excessive traffic is inflicted on servers and networks. The aim is to get the website or server inundated with so many queries that the system is not working and stops working. Here at The Email Shop, you will get to know the best DDoS tool that can help you secure your business operations.
The DDoS breaches are typically utilized by botnets, which are enormous networks of computers. It generally includes PCs infiltrated with a central server managed by (e.g. internet of things) gadgets, servers, desktops, routers, etc. To prevent this, DDoS tools like hulk DDoS are used.
DDoS breaches can potentially come from tens of thousands of non-compromised networked machines. They are either misconfigured or fooled into a botnet despite their regular operation.
The Recon role: The way attackers collect data before a DDoS attack
Attackers use various approaches to get vital information. Understanding these tactics helps you to calculate your organization’s susceptibility to attack. Collecting information requires types of recognition, both direct and indirect.
Best DDoS tool: Direct Recon
Attackers may use tools like Nmap to evaluate a network. In Nmap, all linked devices are identified and a complete evaluation of local and remote networks is shown. The use of Nmap also helps to discover apps that listen to open ports. Network mapping offers an overview of linked devices to attackers.
You Might also Like to Read: ISP DDoS attacks – DDoS Attack Mechanism Scheme in ISP Networks
Physical reconciliation can also be quite helpful. Interestingly, a large amount of the early data collection is offline. Data from the actual world might be essential. All items, including addresses, contact information, pet names, relatives, birthdays, and passwords, are helpful when an attack is planned.
- Shoulder Surfing: This is when unscrupulous people overlook your shoulder to skim information. Training end-users to utilize their information and passwords to safeguard them against theft of sensitive information is incredibly beneficial. This includes teaching strategies in social engineering.
- Dumpster Diving: Attackers commonly use Scarlet papers retrieved from the garbage. By sewing, organizational and individual rubbish, especially that of a high-profile person, sensitive information may readily be retrieved. It is often assumed that shredding is a pain and is often unneeded, yet these little details are a digital gold mine. Physical information shredding takes a long journey to safeguard oneself.
- Organizational activity: Attackers can even take physical recovery from construction activities. Hackers can access a secured physical area and computing equipment by watching who is coming and going and when they frequently enter and go.
Best DDoS tool: Indirect Recon
Indirect reconciliation is carried out to grasp the objective. Similarly, to design effective sales techniques, salespersons examine customer behavior to determine a strategy of attack.
They recognize stuff like this:
Individuals sensitive to social engineering: Attackers use malware or assault a specific network part to take advantage of these individuals.
- Network Settings: Routers, firewalls, and DNS servers are located to enable attackers to analyze the traffic needed to launch an assault.
Current computer networks and any cloud-based technologies are part of this.
- Endpoints: if incorrectly set up, endpoints may be insecure.
- Monocultures: The monoculture may cause considerable damage with less effort.
When a DDoS assailant finds a decent attack surface and identifies a monoculture, they can assault. When attackers perform research, DDoS attacks are often far more successful.
Open-source information is a famous moniker given to indirect recon (OSINT). The traces are not the same as the active instruments, with indirect recognition instruments.
There is the growth of DDoS. They can be volumes-based if a service is swamped with queries or protocol requests depending on the application TCP / IP requests from bogus IP addresses to deplete assets to take down a Website or network infrastructure.
You may potentially become the victim of layer 7, slower and more challenging to detect breaches on applications.
You Might also Like to Read: How to stop DDoS attacks? How to fix the router after a DDoS attack?
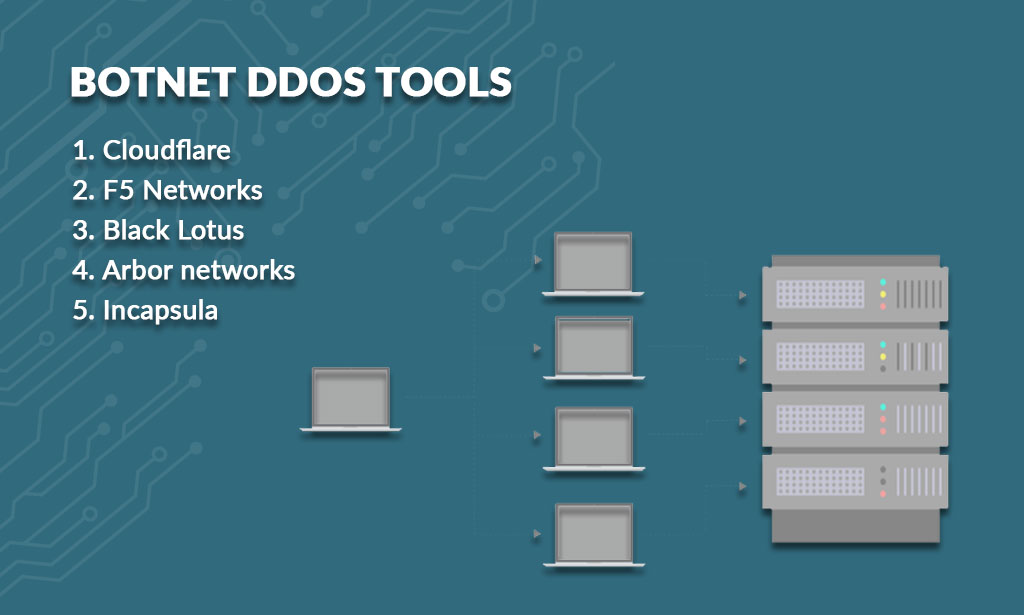
Best botnet DDoS tools to avoid such attacks:
Some of the most significant botnet DDoS tools to protect them from such threats are provided below.
-
Cloudflare
Protection layers 3 and 4 of Cloudflare captivate an assault before reaching a server that does not weigh balancers, firewalls, and routers.
The protection in layer 7 distinguishes between useful and hazardous communications. Includes Cisco, NASDAQ, MIT, and… Cloudflare Clients… The song contest for Eurovision.
-
F5 Networks
Networks of F5 Silverline have an enormous ability to brush traffic and provide on-site security in the cloud or a combination.
It delivers level 3 to 7 protection. Silverline can prevent networks from reaching large capacity and block them from accessing the network of a firm. There is help 24/7.
-
Black Lotus
The company Network Protection Service has been certified and may be labeled white for usage, focusing on the hosting business.
It may be screened and proxied for its Services in layer 4 and requests are mitigated in layer 7. It also has a patent filed on technologies for human comportment analysis to enhance its service.
-
Arbor networks
Arbor Cloud provides cloud protection for cybersecurity both on the Netscout Security Division.
It also provides a cross-terabit traffic cleaning solution and 24/7 help for DDoS via its Operations Center.
-
Incapsula
This year, Incapsula was given a gold medal for its protection service by the Top Ten Assessments ranking site. It has a worldwide network of data centers, which allows it to offer additional scrubbing centers.
It provides complete DDoS protection as an on-site or on-demand solution and a 24/7 security staff.
Conclusion
The tools listed in this article are among the most often DDoS Tools download list. The best DDoS tool can be valuable resources for performance and security testing. At The Email Shop, I have described the DDoS attacks. Here you can get more information about ddos attack tools in kali linux. You can also contact our experts for guidance.