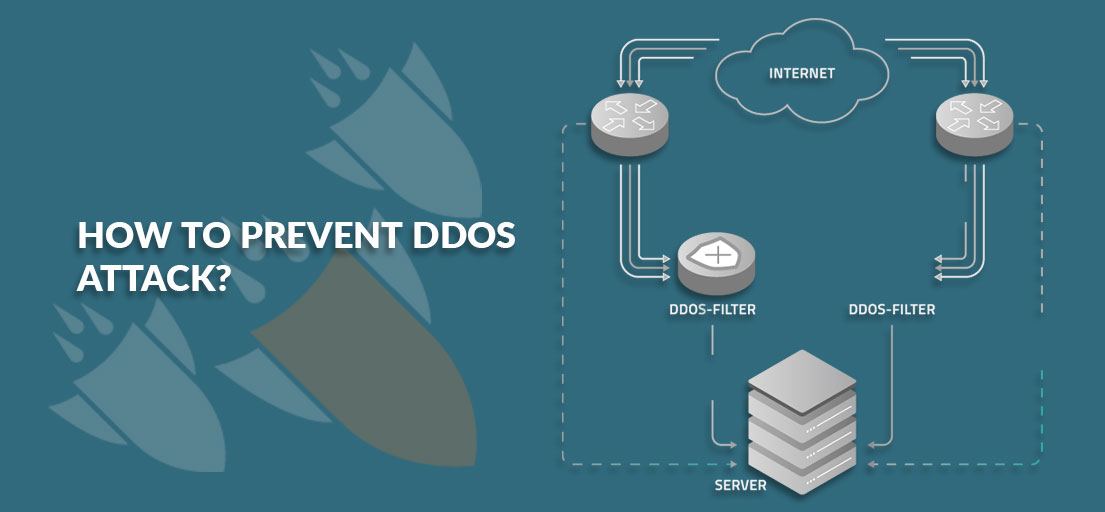
Step by step guide on How to prevent DDoS attack?
Assume doing all the protection defenses that you can take on your site, and currently, you are sure that an attacker cannot get into it. But attackers will nevertheless access your site and harm your business. At The Email Shop, you will understand the DDoS meaning and how to prevent DDoS on PC.
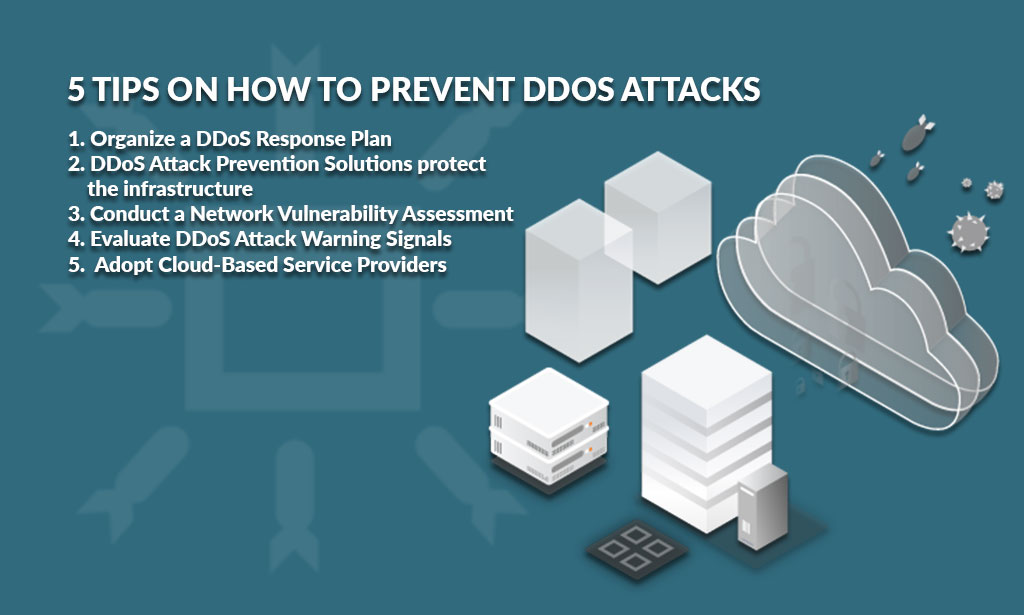
5 Tips on How to Prevent DDoS Attacks
Whether you want to learn How to prevent DDoS attacks on router or how to prevent DoS attacks? Prevention is better medication, and this also implies DDoS attacks. Get ready to avoid a crippling DDoS attack on your company with the following tips.
-
Organize a DDoS Response Plan
Do not blindly get trapped in DDoS attacks; have a contingency plan ready if your company breaks protection so that you can react as soon as possible. Your strategy should document how to work if the DDoS attack succeeds, the technical skills and qualifications required, and a Device Checklist to ensure the advanced identification of threats on your website.
If the DDoS succeeds and identifies obligations such as advising key stakeholders and ensuring coordination across the organization, create an incident management team.
-
DDoS Attack Prevention Solutions protect the infrastructure
Build multi-level security solutions for the network, apps, and facilities. These include firewall, VPN, anti-spam, malware scanning, and other security layers to monitor activities and traffic identification inaccuracies as symptoms of DDoS threats.
Many vendors allow advanced security resources for added charges to be secured by using cloud-based solutions. Other options involve “full cloud” companies with confidential data from a trusted cloud vendor with enhanced virtual and physical protection protocols.
3. Conduct a Network Vulnerability Assessment
Identify network vulnerability before a spiteful user. Threat vulnerabilities are identified in a vulnerability evaluation and help you properly plan for a DDoS attack or other cybersecurity threats in general and patch the infrastructure.
Assessments can protect against vulnerability flaws in the network. This is accomplished by inventing all network equipment and their function, system knowledge, and any related bugs and preparing which devices for enhancements and future evaluation. That will allow you to identify the level of risk of your company to maximize your investment in protection.
You Might also Like to Read: ISP DDoS attacks – DDoS Attack Mechanism Scheme in ISP Networks
-
Evaluate DDoS Attack Warning Signals
You will take steps to minimize harm if you can recognize the signs of the DDoS attack at the earliest time. Spotty connection, poor performance, and occasional web crashes are all signals of DDoS attacks on your business. Train the staff about DDoS signals to alert you to warning signs.
Not all DDoS attack is lengthy and high-volume; short-term, low-volume attacks are just as prevalent. This assault may be particularly disastrous, as it is more likely to go under the radar than a possible security violation as a random occurrence. Low volume DDoS attacks probably could not damage malware. Still, harmful software, including ransomware, will penetrate your network while your IT protection team is busy resolving a low-volume attack.
5. Adopt Cloud-Based Service Providers
The outsourcing of DDoS cloud attack prevention has many advantages.
Cloud services with high cybersecurity standards, such as firewalls and tools for threats detection, can help protect the network and property from DDoS offenders. Cloud capacity is still higher than most private networks, meaning that the DDoS attacks will possibly fail.
Also, well-known cloud services have network replication and duplicate backups of their files, programs, and infrastructure so that you can migrate to stable access to backup models without losing any time when the service is compromised or inaccessible due to a DDoS attack.
Detailed Guide about How to prevent DDoS
Taking adequate security precautions against DDoS with DDoS prevention tools is essential.
DDoS is a non-intrusive attack known as a Distributed Denial of Service attack, making the hacker unnecessary to use the Web for the attack to occur. They carry out the hack without ever cracking into the site remotely.
Rather, they congest the server of your website to interrupt its activity. The most likely website users would not be able to reach your platform and the ones who can meet gradually and randomly.
Why are hackers launching DDoS attacks, and how to prevent DDoS attack on API? The causes are numerous. Hackers usually attempt to break passwords into the site. You start various requests to try various user names and password variations on your login tab. You will overwhelm these requirements on your pages.
More significant DDoS attacks are being launched to target large brands. DDoS attacks also are utilized by hackers for ransom from the companies.
What is the DDOS Attack Classification?
How to stop a DDoS attack? When considering the prevention of these attacks, it is helpful to group them in the form of infrastructure layers (3 and 4) and application layer attacks (6 and 7).
Application Layer 3 and 4 attacks
Layer 3 and 4 attacks are commonly classified as layer attacks on infrastructure. They are a prevalent kind of DDoS attack, including routes such as synchronized floods (SYN) and other attacks such as the User Datagram Packet (UDP) inundations. Such assaults are typically high in number as well as are intended to overwhelm the network or application server capability. But they are luckily easier to detect and straightforward.
You Might also Like to Read: 7 Hosting Server Protection Security Measures
Application 6 and 7 Layer Attacks
6 and 7 Layers are also known as attacks on the application layer. Though less frequent, these attacks are much more complex. Usually, these attacks are limited compared with attacks in the infrastructure layer, but they prefer to concentrate on some costly app modules, making this inaccessible to actual users.
Final words
Would you like to see encryption and how to prevent DDoS with a predictable cloud provider? Do not delay contacting The Email Shop experts for information or a free security risk review about our cloud services. What if you want to go by yourself? Remember that you will face a DDoS attack the next time you see a traffic inflow signaling a business day.